This week’s topic is more on networks as I am trying to study for CS4226 Internet Architecture. Hopefully this can help others who are trying to learn about software defined networks.
What are software defined networks?
Software Defined Networks (SDNs) are a new approach to network management that allows dynamic and and programmable network configuration. This allows improved network performance and monitoring.
Traditional Networking
In traditional networking, equipments are software bundled with hardware. This usually meant that the hardware that you buy locks you into the software which are managed by the hardware manufacturers.
The various manufacturers have their own implementation of a particular protocol. Any new proposed protocol will have to go through the process of getting the hardware manufacturers to implement it. This is a slow process and the hardware manufacturers will only implement it if it is profitable for them to do so.
On top of that, only those specific vendors who have access to the hardware and software of the equipment can innovate on the network. This means that the network is not open to innovation from the community.
As a result, there is slow protocol standardization and slow innovation. Such slow processes can impact the performance, security and reliability of the network.
Operating a large network is expensive. According to Wired, the annual cost of operating a network can be as much as 4 times the cost of the purchase of the network. Some companies even spend 75% of their total budget to maintain and run existing systems.
Routers also contain buggy software. With over 20+ million lines of code, it is not surprising that there are bugs in the software. This can lead to security vulnerabilities and network outages.
This is where Software Defined Networks (SDNs) come in.
Core of networking
In the core of networking, there are 2 key features.
- Running routing algorithms / protocols (RIP, OSPF, BGP, etc)
- Forwarding data packets from incoming links to outgoing links
These 2 categories can be split up into 2 different sections.
- Data Plane
- Control Plane
We can think of routers of having both a data and a control plane and switches as only having a data plane.
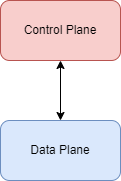
The data plane deals with the delivering of packets and the control plane deals with the routing.
Data plane
The data plane deals with the processing and delivering of network packets based on the internal state of routers. This is the part of the network that is responsible for forwarding packets from incoming links to outgoing links.
This is on relatively fast time scales (per packet) which happens very quickly and many times per second.
Control plane
The control plane determines how and where packets are forwarded to. This includes the routing, network engineering and firewall.
This is also where all the networking algorithms run (BGP, OSPF, RIP, etc)
These happens on a relatively slow time scale (per control event)
Principles of Software Defined networks
These are the main principles of software defined networks
- Disaggregation
- Centralized Control
- Programmability
We will be diving into each of the principles in detail below.
Disaggregation
Disaggregation is the separation of the control plane and the data plane. This allows a network operator to independently source and purchase control and data planes from different vendors.
The data plane generally consists of cheaper commodity forwarding devices (bare-metal switches) and the control plane consists of software which control these switches.
In order to achieve this, there is a need to define a forwarding abstraction layer. This layer is a general purpose way for the control plane to tell the data plane to forward packets in a particular way.
An example of this will be OpenFlow’s Flow rules. This is an open-source general purpose way for the control plane to tell the data plane to forward packets in a particular way.
In Openflow, a flow rule is a Match-Action pair. Any packets that match will have the action applies to it.
Let us demonstrate this using the table below
| Match | Action |
|---|---|
| Ingress Port = 1 | Output Port = 2 |
| Ingress Port = 2 | Output Port = 1 |
| Ingress Port = 3 | Drop |
In the above table, we can see that any packets that come in through port 1 will be forwarded to port 2 and any packets that come in through port 2 will be forwarded to port 1. Any packets coming from port 3 will be dropped.
The actual configuration consists of many more rules and actions for the network operator to configure.
Benefits
The benefits of disaggregation are as follows:
- Hardware and software can be independently sourced and purchased
- Hardware and software can be independently upgraded
- Innovation can happen in parallel on both the hardware and software
An analogy can be made to the PC industry. The PC industry has been disaggregated for a long time. The CPU, RAM, Motherboard, GPU, etc are all sourced from different vendors. This allows for innovation to happen in parallel on the CPU, RAM, Motherboard, GPU, etc.
Likewise, after you have built your computer, the computer, operating system and applications can all evolve independently from one another due to disaggregation.
Centralized Control
Before we talk about centralized control let us talk about the difference between control and configuration.
Control Vs Configuration
Control is the process of making real-time decisions on how to respond to link / switch failures. The control plane is required to learn about the failure and provide a remedy immediately.
Configuration is the process of setting up the network devices. This can be seen as setting up a new flow rule in SDNs.
Why Centralized Control?
When discussing about the control plane, we can either have a centralized control plane or a on-switch (Distributed) control plane.
On-Switch control planes means that the switches are operating separately and independently from one another. The state of each switch is not shared with the other switches.
Centralized control planes means that the switches are operating in a centralized manner. The state of each switch is shared to a controller who will be making decisions on how to forward packets.
Centralized control planes come with a host of benefits
Pros and Cons of Centralized Control
Benefits
- It removes the complexity of managing distributed systems (EG: In OSPF, RIP, other routing protocols)
- Able to make decisions based on the entire network topology instead of just with local information.
Disadvantages
- There will be a single point of failure.
To address the disadvantages, the centralized controller is only logically centralized instead of physically centralized. This means that the controller can make use of distributed system techniques to ensure that the controller is highly available.
Programmability
Programmability is the ability to configure the network programmatically. This allows for the network to be configured in a more dynamic and flexible manner.
Network programmers can make use of programs to create different rules for the network to forward packets. This includes but is not limited to the following.
- Load balancing
- Setting up firewalls
- Forwarding packets with switch loops
Load balancing
As the centralized controller is able to see all the network traffic in the network, they are able to optimized and send network packets on other paths when they detect a network congestion.
Setting up firewalls
The controller can match packets to a set of rules and apply actions to the packets. This allows for the creation of firewalls where packets which fit a certain set of rules can be dropped.
Forwarding packets with switch loops
Imagine a series of switches connected in a triangle. In a traditional setup, there is a possibility where each switch thinks that the destination is from the next switch. This can lead to a switch loop where the packets are forwarded in a loop infinitely within the switch and never reach the destination.
With software defined networking, the controller can choose to forward the packet based on the network architecture that it sees. This allows for the controller to break the switch loop and forward the packet to the destination.
Benefits of programmability
- Allows for the network to be configured in a more dynamic and flexible manner
- Performance optimizations
- Rapid innovation and fast evolution
- Supports change of protocol in the future, without having to change the hardware
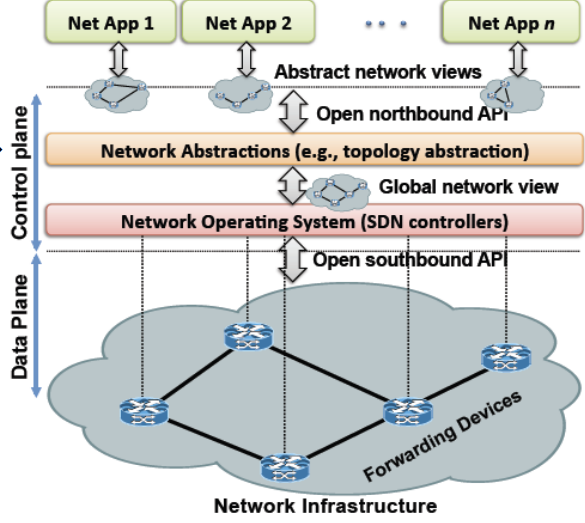
Network Operating Systems
All of the above is generally implemented using a Network operating system. This is a software that runs on the controller and is responsible for managing the network. It sits just on top of the control plane and is a foundation for building control applications which are deployed on the network.
Summary
In this article, we have covered the following
- Principles of Software defined networking
- Separation of Control Plane and Data Plane
- Logically Centralized Control
- Programmability
All of the principle above makes use of abstractions
- Specification abstraction
- Allows a controller to express the desired network behavior without implementing it
- EG: Openflow rules
- Distribution abstraction
- Shield SDN from the distributed states, making the distributed control logically centralized
- Using distributed systems techniques to ensure that the controller is highly available
- Forwarding abstraction
- Allow forwarding behavior by apps while hiding the details of the forwarding hardware.
For a more in-depth explanation, you can check out Software-Defined Networking: A Comprehensive Survey.
Main users of SDNs
There are 3 main categories of users of SDNs:
- Cloud Providers (EG: Google, Facebook, Microsoft, etc)
- Network operators (EG: Comcast, AT&T, NTT, etc)
- Enterprises (EG: Universities and companies)
Use Cases of SDNs
These are the use cases of SDN
- Network Virtualization
- Switching Fabrics
- Traffic Engineering
- Software Defined WANs
- Last-mile access networks
- Software-Defined Internet exchanges (SDX)
- Mobility and wireless
- Security, measurement and monitoring
We will be taking a look at some of them (those in bold) in detail below.
Network Virtualizations
Before we talk about network virtualization, let us talk about some of the current virtualization technology to draw an analogy.
Current Virtualization technologies
Some current technology for hardware virtualization::
- Virtual Machines (VMs)
- Containers
These technologies seek to virtualize the hardware resources of a computer. For example, a VM is a virtual computer that runs on top of a physical computer. It is able to do so by virtualizing the hardware resources of the physical computer.
For networks:
- Virtual Private Networks (VPNs)
- Virtual Local Area Networks (VLANs)
These technologies seek to virtualize the network resources of a computer. For example, a VPN is a virtual network that runs on top of a physical network. It is able to do so by virtualizing the network resources of the physical network.
What is network virtualization?
Network Virtualization is similar to the ones state above but done in terms of network infrastructure. It can divide 1 physical network into multiple virtual networks or divide a big network into multiple smaller independent virtual networks.
How does network virtualization work?
This is done by virtualizing the network resources of the physical network similar to how a virtual machine virtualize the hardware resources of a physical computer.
For the first time, cloud providers are able to virtualize networks for other users to use. Enterprises can now rent network from cloud providers to set up their own virtual networks without knowing the underlying network infrastructure.
Benefits of Network Virtualization
- Reduces network provisioning time from weeks to minutes
- Achieve greater operational efficiency by automating network provisioning
- Improve network security by isolating different virtual networks
Switching Fabrics
Switching fabrics are the network infrastructure that connects the servers in a data center. Using SDNs, switching fabrics can be virtualized.
Within data centers, they typically make use of Leaf-Spine topology. Spines are the core switches that connect to the leaf switches. Leaf switches are the switches that connect to the servers.
Usually strong switches are used for the spines and weaker switches are used for the leaf switches.
With the introduction of SDNs, it makes it easier to connect virtual switch networks to physical network devices.
The network administrator will only have to manage from the controller software to configure the virtual switches rather than login to each of the switch to configure them.
Traffic Engineering
Traffic engineering is a method of optimizing the performance of a network by analyzing, predicting, and regulating the behavior of traffic flows.
With SDNs, traffic engineering can be done in a more efficient way as the controller will now have a global view of the data instead of local view from the point of view of switches.
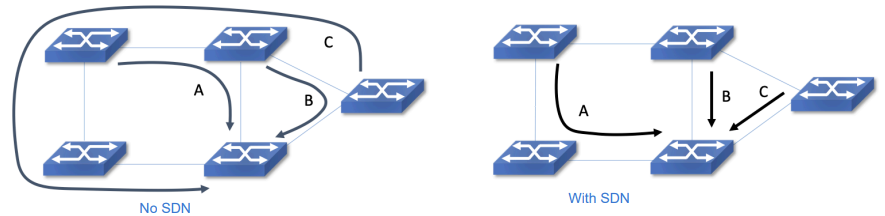
In this example, instead of each switch having to decide which path to take based on ARP requests, the controller will be able to decide which path to take for each flow to arrive at the destination the quickest.
Software Defined WANs (SD-WAN)
Software Defined Wide Area Networks is a virtualized service that connects and extends enterprise networks over large geographical distances.
Before we take a deep dive into SD-WANs, let us first talk about the current WAN technology.
Current WAN technology
Traditional WANs are based on conventional routers and switches. It spans beyond a single location and connects multiple locations together. The most common WAN is the internet of today.
Purpose of WANs
The main purpose of WANs include
- Communication using voice and video
- Share resources between different devices
- Running applications
How does SD-WAN improve on WANs?
SD-WAN enables the WAN to be more flexible and dynamic. It can be configured to use the best path for each flow to arrive at the destination the quickest.
It does this by separating applications from the underlying network services with a policy-based virtual overlay. It abstracts away all the details of the network layer and allows the WAN to use a variety of different connection types interchangeably.